Purpose
The bash script getWebserverNames.sh connects to a SSL/TLS server on a specifiable TCP port and display information about the presented certificate.
Information that are shown:
- The issuer of the certificate.
- The date up to which the certificate is valid.
- The subject of the certificate.
- It’s subject alternate names (SAN).
- The certificate chain presented by the server.
Requirements
- It is tested on MacOS and Linux
opensslis on MacOS and most Linux distribution installed.- The
Bashshell should be available on any Linux distribution and currently is available on MacOS (which might change in the future). - Since
seddiffer between most Linux distribution and MacOS and has different syntax, this script tries to discover whichsedis installed and use the apropriate syntax.
Example
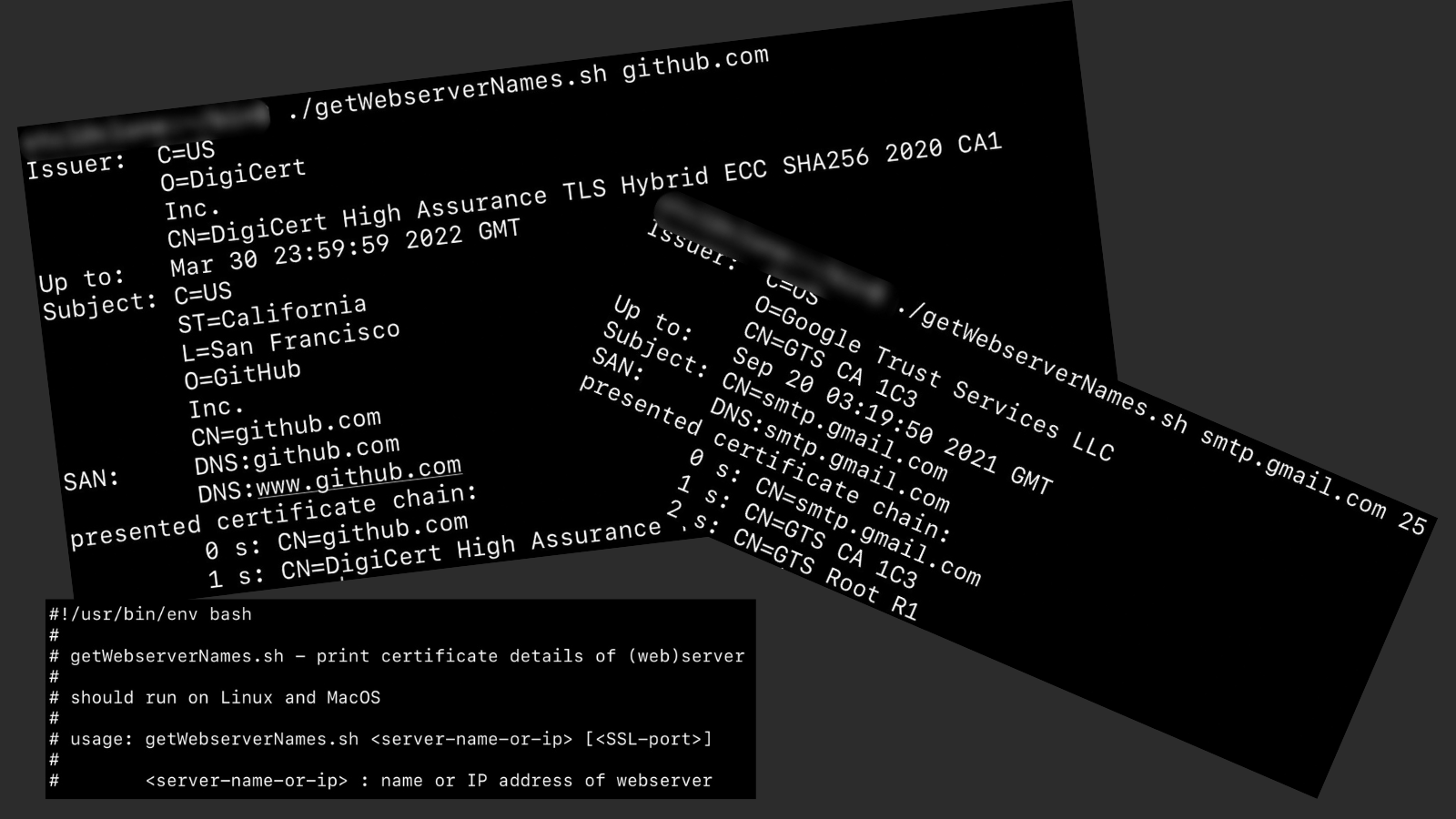
~$ openSSLscripts/getWebserverNames.sh github.com
Issuer: C=US
O=DigiCert
Inc.
CN=DigiCert High Assurance TLS Hybrid ECC SHA256 2020 CA1
Up to: Mar 30 23:59:59 2022 GMT
Subject: C=US
ST=California
L=San Francisco
O=GitHub
Inc.
CN=github.com
SAN: DNS:github.com
DNS:www.github.com
presented certificate chain:
0 s: CN=github.com
1 s: CN=DigiCert High Assurance TLS Hybrid ECC SHA256 2020 CA1
Some explanations
openssl s_client
- Connects to a SSL/TLS server (like “
telnet server port”, but SSL/TLS encrypted)
and - as a side effect - gives several information of the active SSL/TLS-session including the certificate(s). - in script:
openssl s_client $EXTRAOPTS -showcerts -connect $SERVERADDRESS:$SERVERPORT-showcertsadds the full certificate chain to the output, otherwise only the server’s certificate is shown.-starttls smtpuses a SMTP dialog to connect in cleartext and then sendsSTARTTLSto switch to SSL/TLS and finaly will get the certificate
- Examples:
openssl s_client -connect www.example.com:443openssl s_client -showcerts -starttls smtp -connect mail.example.com:25
openssl x509
- Displays or manipulates certificate information provided either on stdin or from file, if
-in filenameis specified. - By default it expects PEM encoded certificates (= everyting between
-----BEGIN CERTIFICATE-----
and-----END CERTIFICATE-----). - It usually handles only the first certificate, if multiple are presented.
- in script:
openssl x509 -noout -text-nooutsupresses the certificate output in “binary” format (by default PEM).-textprints the certificate’s information in plain text.
sed
- The
sedcommands on Linux and MacOS are different (= have different options / syntax), so we have to test which one is running.
if sed --version 2>/dev/null | head -1 | grep -q GNU - On MacOS the syntax looks a bit complex to replace all comma+space combinations (
,) with new lines and an indentation:Thesed $'s/,/\\\n /g'$'...'expands the escape sequences in the quote:\\converts to a real\.\nconverts to a newline.\<newline>is send to sed.- it needs to be escaped for sed, so sed won’t end, but show the newline-
Link
This script is included in my git repository openSSLscripts hosted at GitHub:
- Browser access: (https://github.com/stclj/openSSLscripts)
- Clone by HTTPS:
git clone https://github.com/stclj/openSSLscripts.git - Clone by SSH:
git clone git@github.com:stclj/openSSLscripts.git